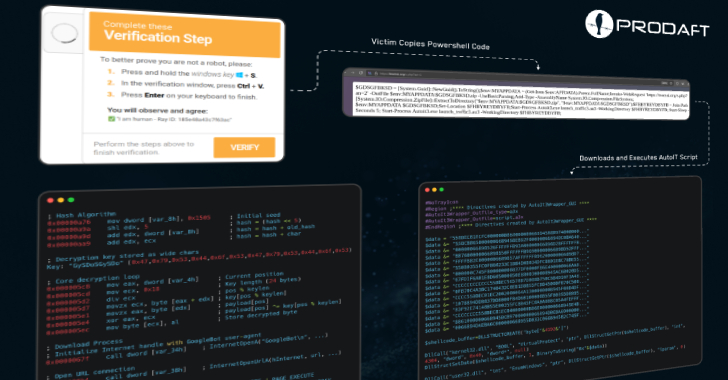
CastleLoader Malware Infects 469 Devices Using Fake GitHub Repos and ClickFix Phishing
Cybersecurity researchers have shed light on a new versatile malware loader called CastleLoader that has been put to use in campaigns distributing various information stealers and remote access trojans (RATs). The activity employs Cloudflare-themed ClickFix phishing attacks and fake GitHub repositories opened under the names of legitimate applications, Swiss cybersecurity company PRODAFT said in
Cyber News