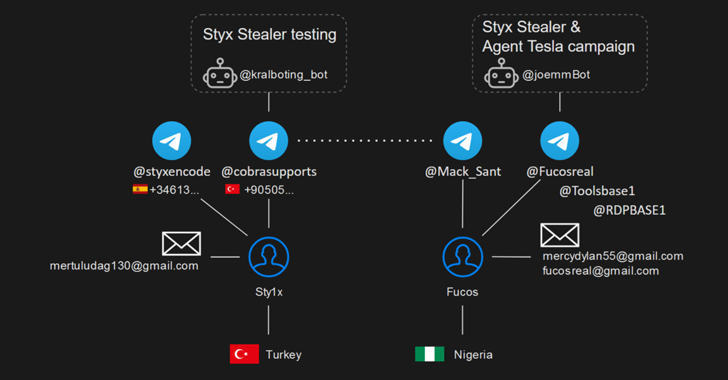
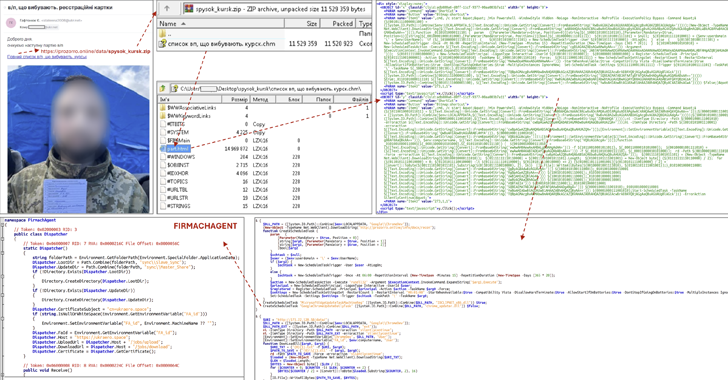
Story of an Undercover CIA Agent who Penetrated Al Qaeda
Rolling Stone has a long investigative story (non-paywalled version here) about a CIA agent who spent years posing as an Islamic radical. Unrelated, but also in the “real life spies” file: a fake Sudanese diving resort run by Mossad. Tags: al Qaeda, CIA, espionage, undercover Sidebar photo of Bruce Schneier by Joe MacInnis.
Cyber News