⚡ THN Weekly Recap: Top Cybersecurity Threats, Tools and Tips [3 February]
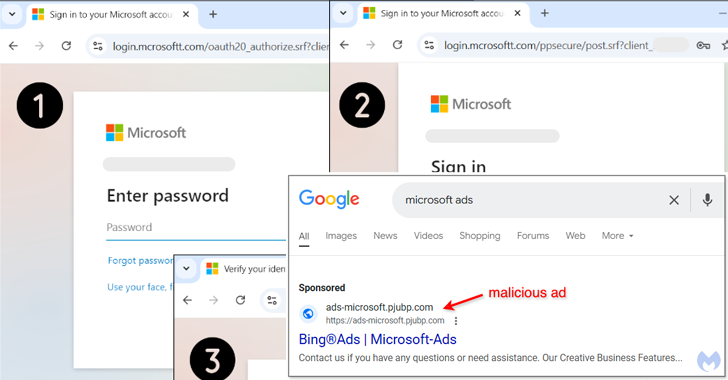
This week, our news radar shows that every new tech idea comes with its own challenges. A hot AI tool is under close watch, law enforcement is shutting down online spots that help cybercriminals, and teams are busy fixing software bugs that could let attackers in. From better locks on our devices to stopping sneaky […]
Cyber News