Iran-Linked MuddyWater Deploys Atera for Surveillance in Phishing Attacks
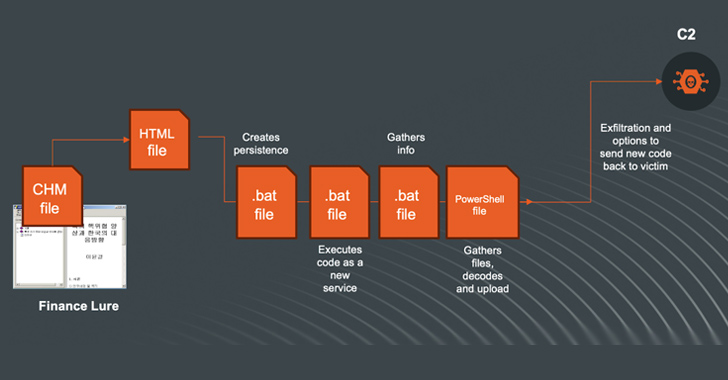
The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring and Management (RMM) solution called Atera. The activity, which took place from March 7 through the week of March 11, targeted Israeli entities spanning […]
Cyber News