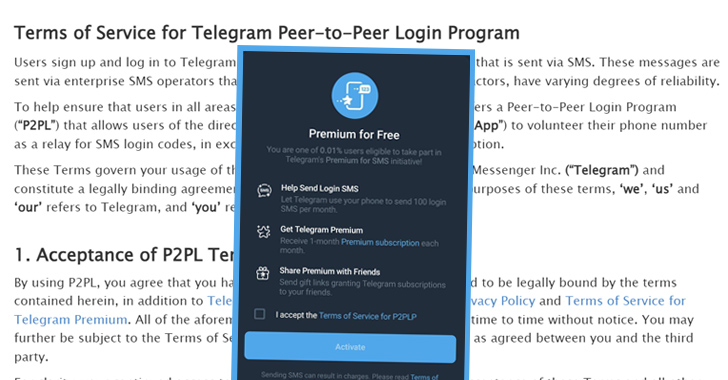
Telegram Offers Premium Subscription in Exchange for Using Your Number to Send OTPs
In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends’ email addresses in exchange for free pizza. “Whereas people say they care about privacy, they are willing to relinquish […]
Cyber News