Ukraine Targeted in Cyberattack Exploiting 7-Year-Old Microsoft Office Flaw
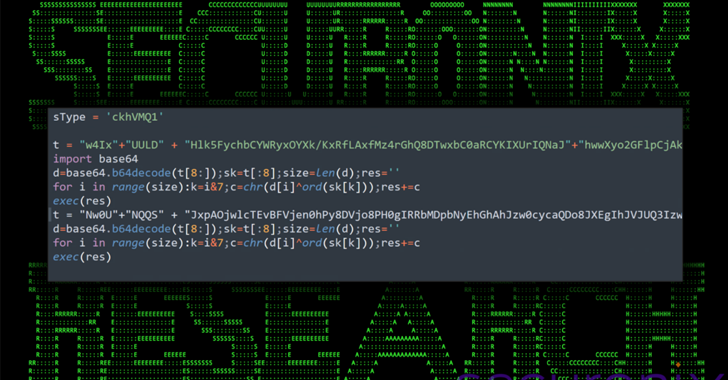
Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The attack chain, which took place at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file (“signal-2023-12-20-160512.ppsx”) as the starting point, with the […]
Cyber News