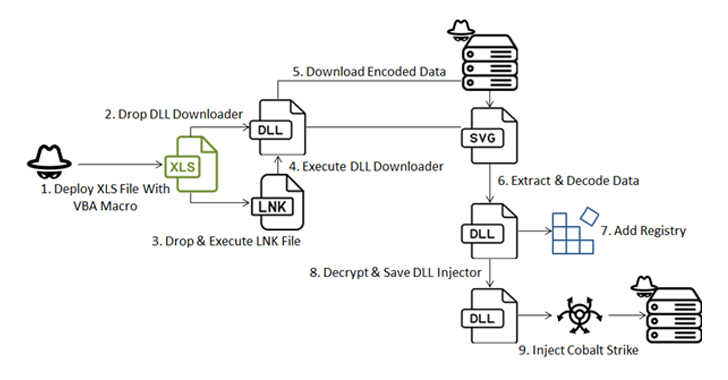
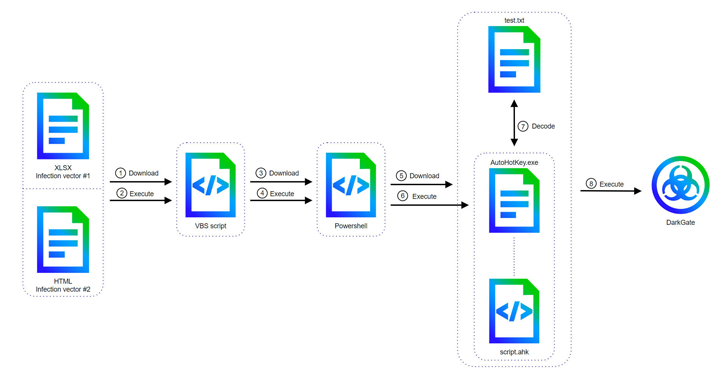
Breaking a Password Manager
Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password. Grand and Bruno spent months reverse engineering the version of the RoboForm program that they thought Michael had used in 2013 and found that the pseudo-random number generator used to generate passwords in that version—and subsequent […]
Cyber News