Cryptojacking Campaign Targets Misconfigured Kubernetes Clusters
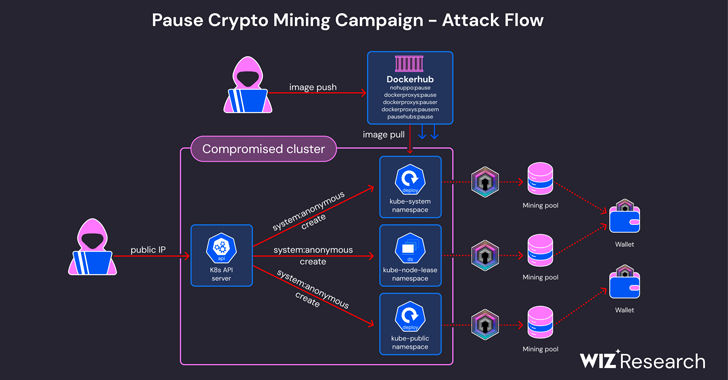
Cybersecurity researchers have warned of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters to mine Dero cryptocurrency. Cloud security firm Wiz, which shed light on the activity, said it’s an updated variant of a financially motivated operation that was first documented by CrowdStrike in March 2023. “In this incident, the threat actor abused anonymous access […]
Cyber News