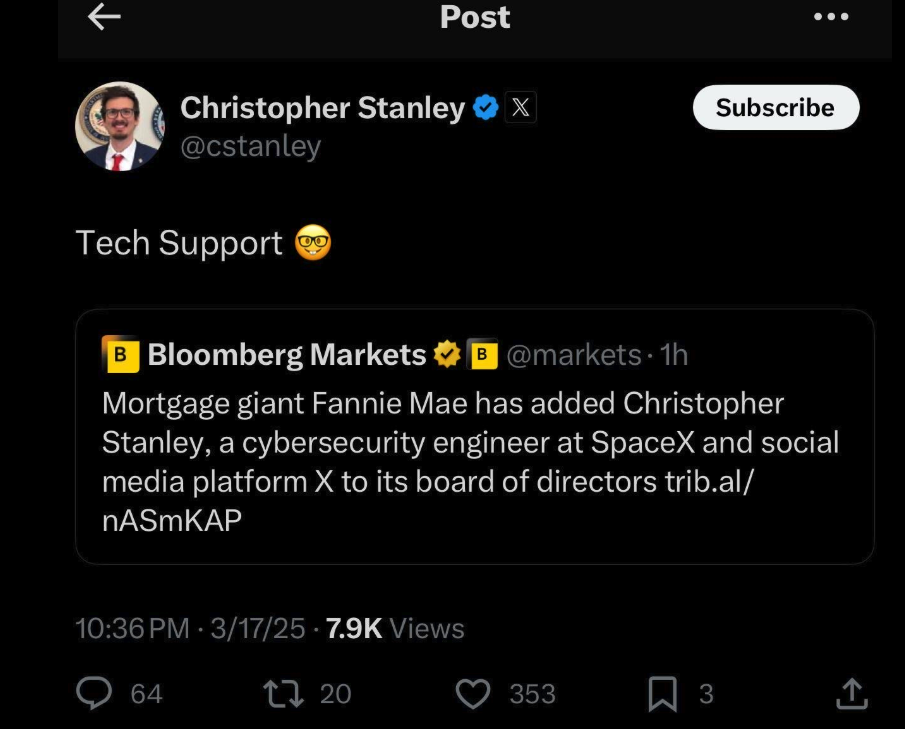
DOGE to Fired CISA Staff: Email Us Your Personal Data
A message posted on Monday to the homepage of the U.S. Cybersecurity & Infrastructure Security Agency (CISA) is the latest exhibit in the Trump administration’s continued disregard for basic cybersecurity protections. The message instructed recently-fired CISA employees to get in touch so they can be rehired and then immediately placed on leave, asking employees to […]
Cyber News