Free Sniper Dz Phishing Tools Fuel 140,000+ Cyber Attacks Targeting User Credentials
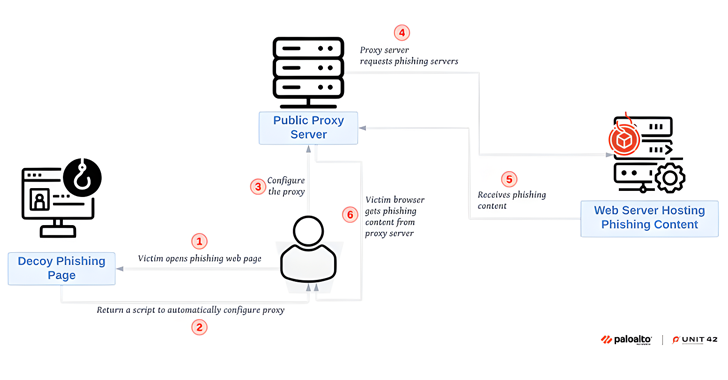
More than 140,000 phishing websites have been found linked to a phishing-as-a-service (PhaaS) platform named Sniper Dz over the past year, indicating that it’s being used by a large number of cybercriminals to conduct credential theft. “For prospective phishers, Sniper Dz offers an online admin panel with a catalog of phishing pages,” Palo Alto Networks […]
Cyber News