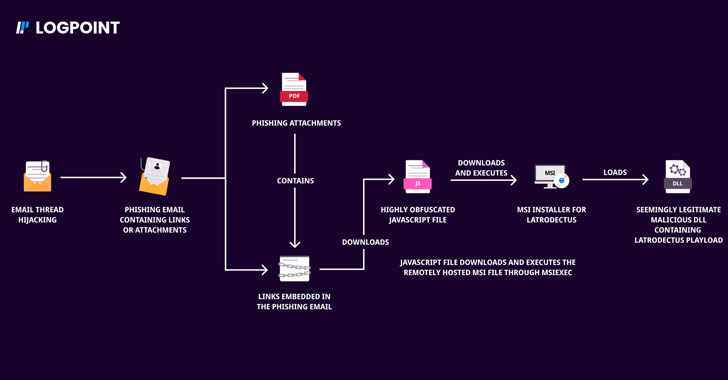
A Comprehensive Guide to Finding Service Accounts in Active Directory
Service accounts are vital in any enterprise, running automated processes like managing applications or scripts. However, without proper monitoring, they can pose a significant security risk due to their elevated privileges. This guide will walk you through how to locate and secure these accounts within Active Directory (AD), and explore how Silverfort’s solutions can help […]
Cyber News