Microsoft Confirms Server Misconfiguration Led to 65,000+ Companies’ Data Leak
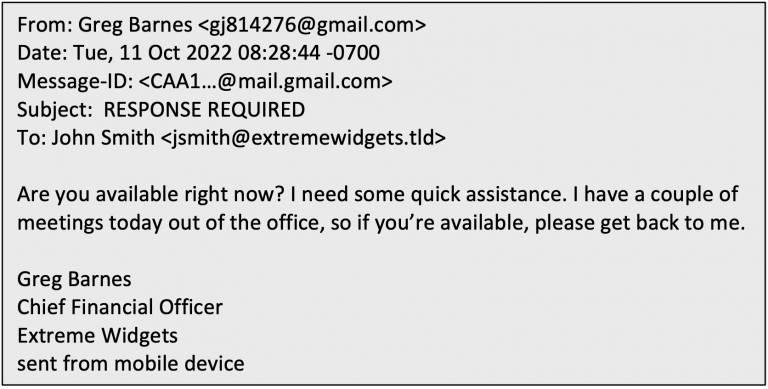
Microsoft this week confirmed that it inadvertently exposed information related to thousands of customers following a security lapse that left an endpoint publicly accessible over the internet sans any authentication. “This misconfiguration resulted in the potential for unauthenticated access to some business transaction data corresponding to interactions between Microsoft and prospective
Cyber News, Cyber Threat Trends