Prefix Lists in Network Rules to Access AWS Services Without CIDRs
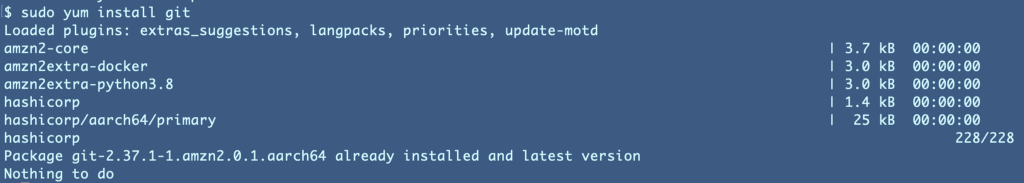
ACM.103 Provide access to S3 (and yum) in network rules without adding every S3 CIDR to maintain zero-trust networking This is a continuation of my series on Automating Cybersecurity Metrics. In the last post, I showed you how to access Git using a static IP addess (otherwise known as an EIP on AWS to add […]
Cyber News, Cyber Threat Trends