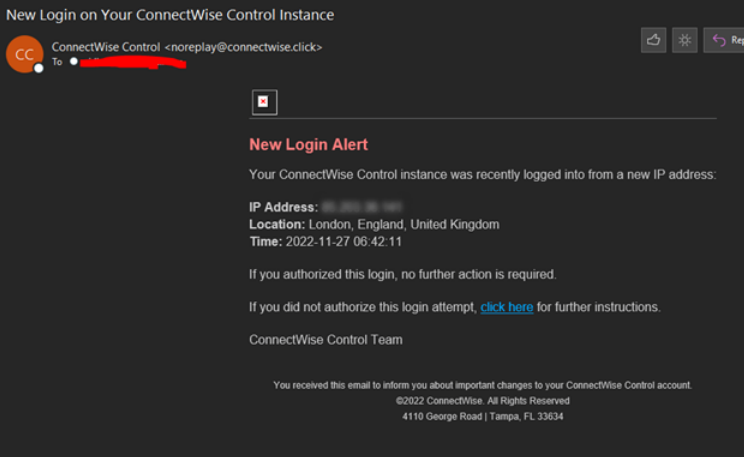
ConnectWise Quietly Patches Flaw That Helps Phishers
ConnectWise, a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning about an unusually sophisticated phishing attack that can let attackers take remote control over user systems when recipients click the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it […]
Cyber News, Cyber Threat Trends