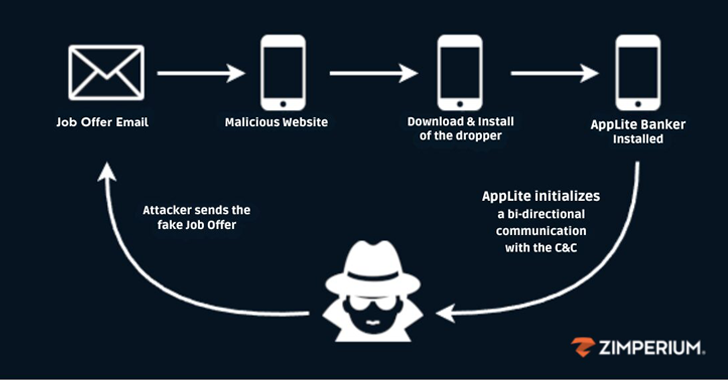
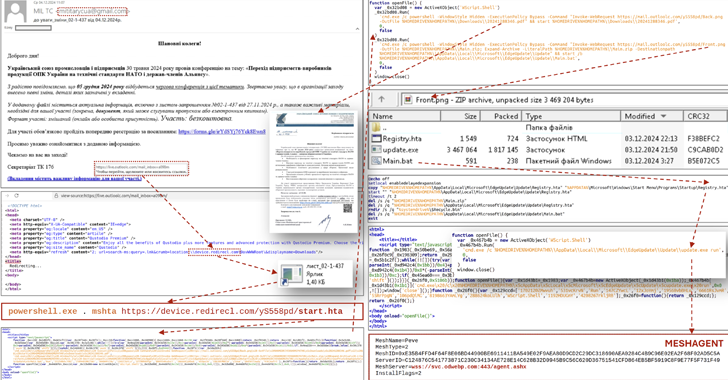
Fake Recruiters Distribute Banking Trojan via Malicious Apps in Phishing Scam
Cybersecurity researchers have shed light on a sophisticated mobile phishing (aka mishing) campaign that’s designed to distribute an updated version of the Antidot banking trojan. “The attackers presented themselves as recruiters, luring unsuspecting victims with job offers,” Zimperium zLabs Vishnu Pratapagiri researcher said in a new report. “As part of their fraudulent hiring process, the […]
Cyber News