Researchers Uncover Espionage Tactics of China-Based APT Groups in Southeast Asia
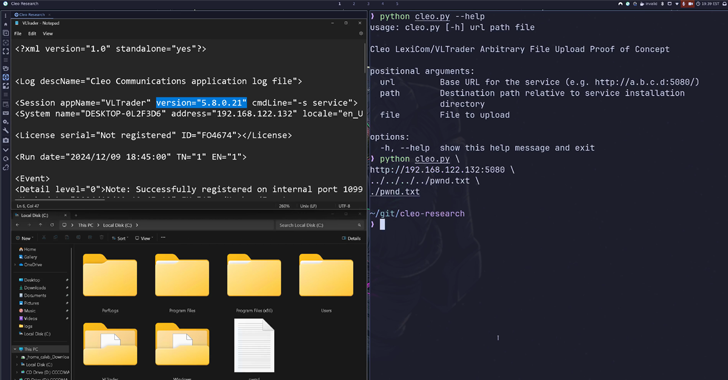
A suspected China-based threat actor has been linked to a series of cyber attacks targeting high-profile organizations in Southeast Asia since at least October 2023. The espionage campaign targeted organizations in various sectors spanning government ministries in two different countries, an air traffic control organization, a telecoms company, and a media outlet, the Symantec Threat […]
Cyber News