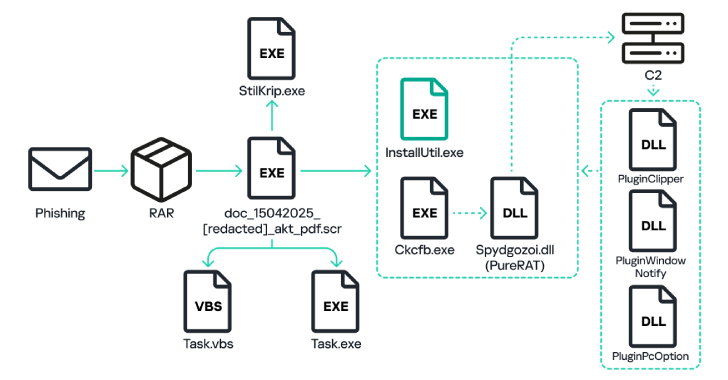
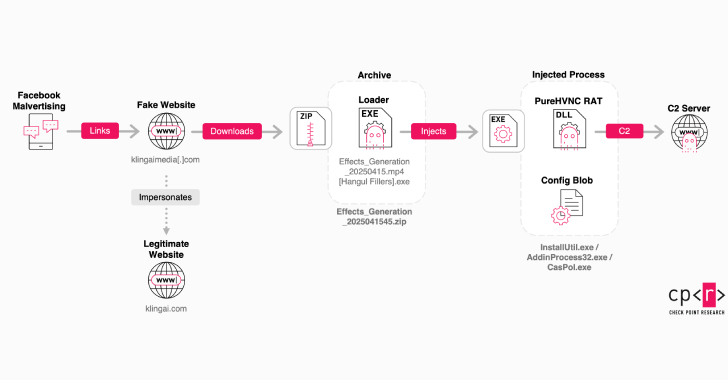
Russian Hackers Exploit Email and VPN Vulnerabilities to Spy on Ukraine Aid Logistics
Russian cyber threat actors have been attributed to a state-sponsored campaign targeting Western logistics entities and technology companies since 2022. The activity has been assessed to be orchestrated by APT28 (aka BlueDelta, Fancy Bear, or Forest Blizzard), which is linked to the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center, Military […]
Cyber News