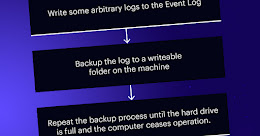
CloudFormation cannot update a stack when a custom-named resource requires replacing
Should this issue be handled by CloudFormation automatically behind the scenes? I added a customer managed prefix list to a security group and then I started getting this error message: CloudFormation cannot update a stack when a custom-named resource requires replacing This is a very strange error message to me. What exactly is a custom-named resource? I […]
Cyber News, Cyber Threat Trends