UAT-5918 Targets Taiwan’s Critical Infrastructure Using Web Shells and Open-Source Tools
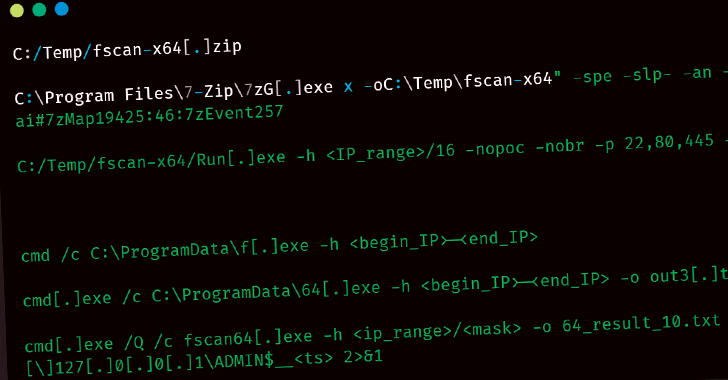
Threat hunters have uncovered a new threat actor named UAT-5918 that has been attacking critical infrastructure entities in Taiwan since at least 2023. “UAT-5918, a threat actor believed to be motivated by establishing long-term access for information theft, uses a combination of web shells and open-sourced tooling to conduct post-compromise activities to establish persistence in […]
Cyber News