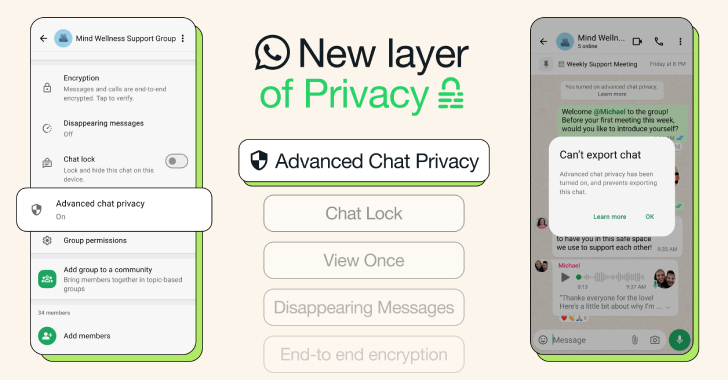
WhatsApp Adds Advanced Chat Privacy to Blocks Chat Exports and Auto-Downloads
WhatsApp has introduced an extra layer of privacy called Advanced Chat Privacy that allows users to block participants from sharing the contents of a conversation in traditional chats and groups. “This new setting available in both chats and groups helps prevent others from taking content outside of WhatsApp for when you may want extra privacy,” […]
Cyber News