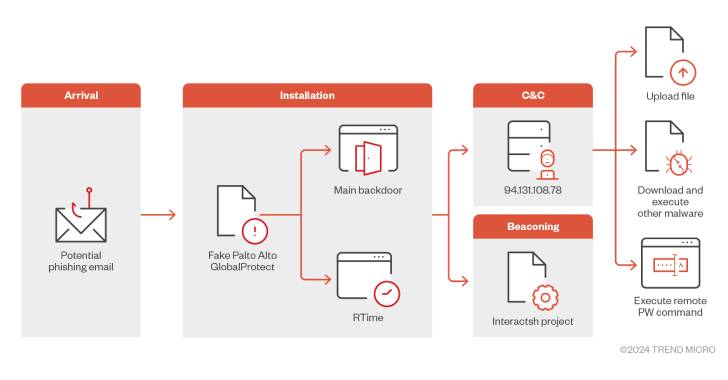
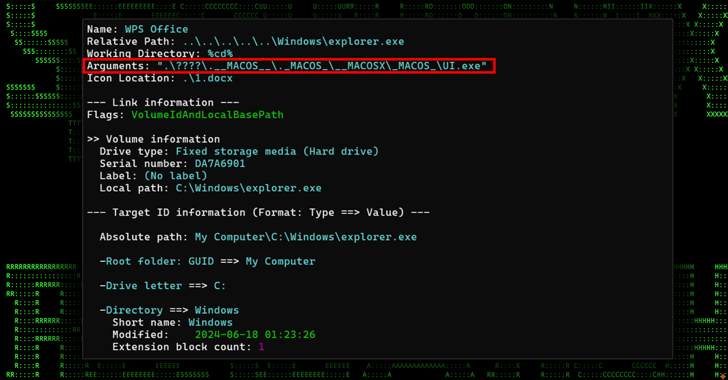
North Korean Hackers Deploy FudModule Rootkit via Chrome Zero-Day Exploit
A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the FudModule rootkit. The development is indicative of the persistent efforts made by the nation-state adversary, which has made a habit of incorporating rafts of Windows zero-day […]
Cyber News