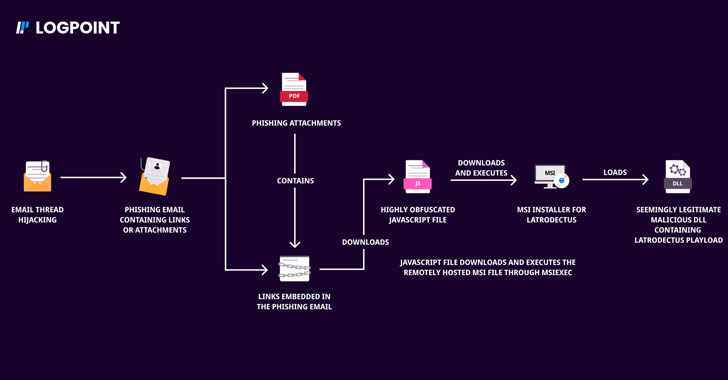
Bumblebee and Latrodectus Malware Return with Sophisticated Phishing Strategies
Two malware families that suffered setbacks in the aftermath of a coordinated law enforcement operation called Endgame have resurfaced as part of new phishing campaigns. Bumblebee and Latrodectus, which are both malware loaders, are designed to steal personal data, along with downloading and executing additional payloads onto compromised hosts. Tracked under the names BlackWidow, IceNova, […]
Cyber News