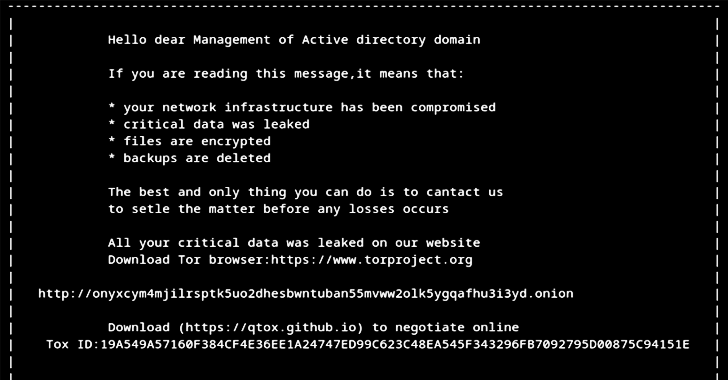
New ‘Helldown’ Ransomware Variant Expands Attacks to VMware and Linux Systems
Cybersecurity researchers have shed light on a Linux variant of a relatively new ransomware strain called Helldown, suggesting that the threat actors are broadening their attack focus. “Helldown deploys Windows ransomware derived from the LockBit 3.0 code,” Sekoia said in a report shared with The Hacker News. “Given the recent development of ransomware targeting ESX, […]
Cyber News