VexTrio: The Uber of Cybercrime – Brokering Malware for 60+ Affiliates
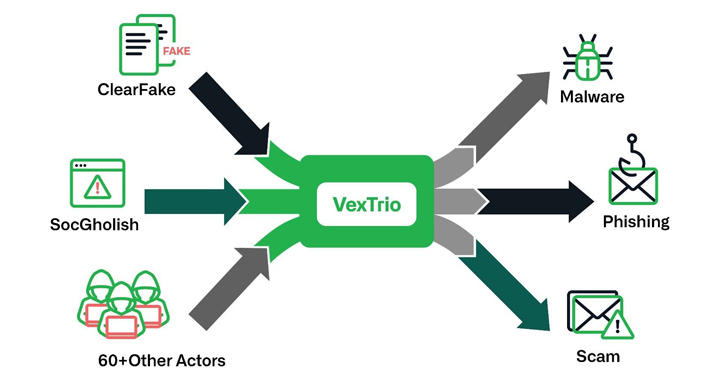
The threat actors behind ClearFake, SocGholish, and dozens of other e-crime outfits have established partnerships with another entity known as VexTrio as part of a massive “criminal affiliate program,” new findings from Infoblox reveal. The latest development demonstrates the “breadth of their activities and depth of their connections within the cybercrime industry,” the company said, […]
Cyber News