Revolutionizing High-Level Cybersecurity Risk Assessment with AI
Revolutionizing High-Level Cybersecurity Risk Assessment with AI The fusion of artificial intelligence (AI) with cybersecurity is akin to putting on a pair of infrared goggles in a dark room. Suddenly, risks that once lurked unseen in the shadows become glaringly apparent, offering organizations the opportunity to bolster their defenses and outmaneuver digital adversaries. The Changing […]
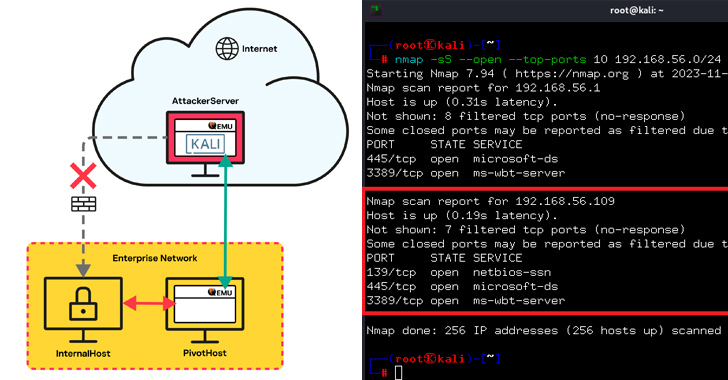
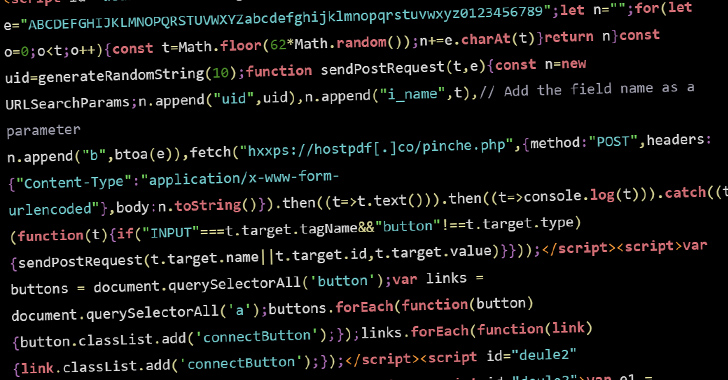
High-Level Risk Assessment