RedCurl Cybercrime Group Abuses Windows PCA Tool for Corporate Espionage
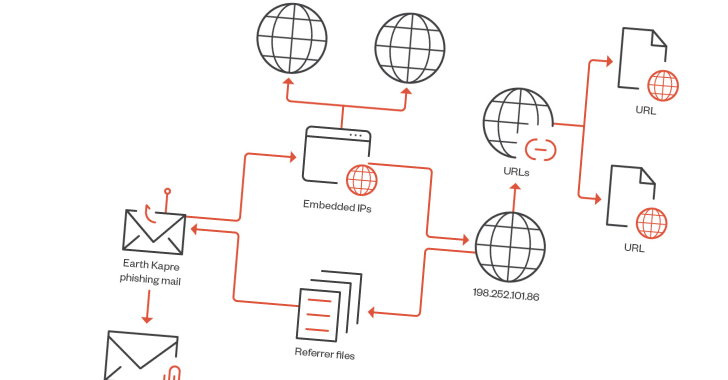
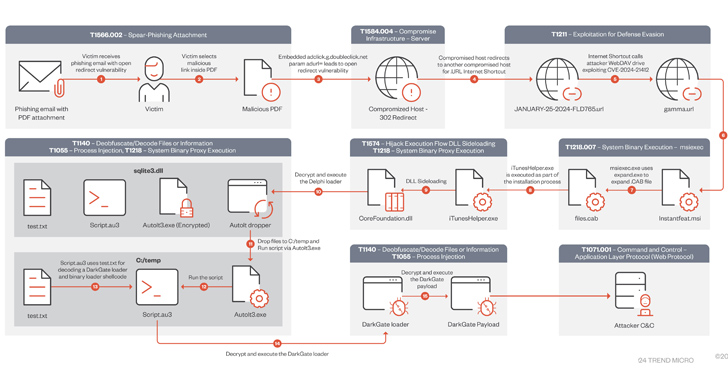
The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) to execute malicious commands. “The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and address compatibility issues with older programs,” Trend Micro said in an analysis published this month. “Adversaries can exploit […]
Cyber News