Critical Unpatched Ray AI Platform Vulnerability Exploited for Cryptocurrency Mining
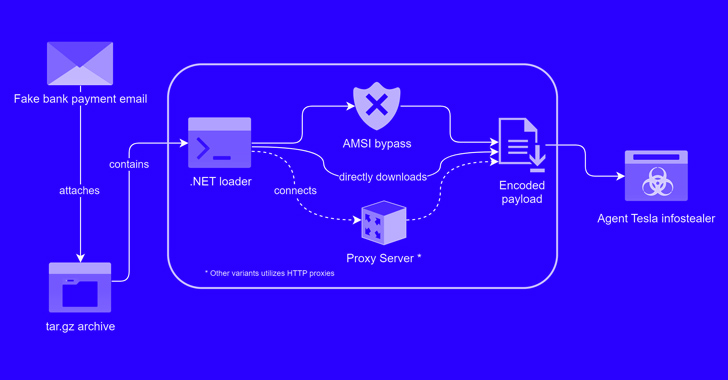
Cybersecurity researchers are warning that threat actors are actively exploiting a “disputed” and unpatched vulnerability in an open-source artificial intelligence (AI) platform called Anyscale Ray to hijack computing power for illicit cryptocurrency mining. “This vulnerability allows attackers to take over the companies’ computing power and leak sensitive data,” Oligo Security researchers Avi Lumelsky, Guy Kaplan, […]
Cyber News