Mispadu Trojan Targets Europe, Thousands of Credentials Compromised
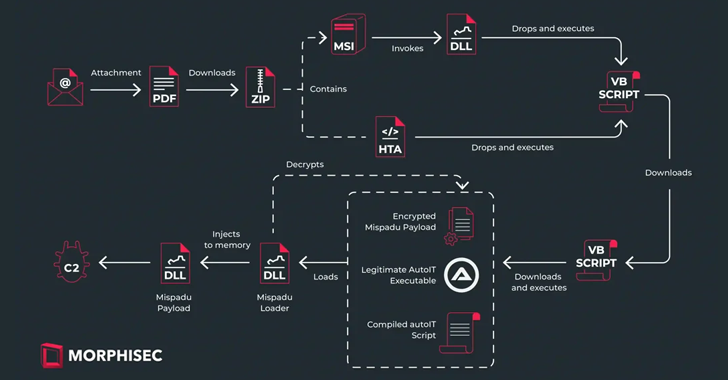
The banking trojan known as Mispadu has expanded its focus beyond Latin America (LATAM) and Spanish-speaking individuals to target users in Italy, Poland, and Sweden. Targets of the ongoing campaign include entities spanning finance, services, motor vehicle manufacturing, law firms, and commercial facilities, according to Morphisec. “Despite the geographic expansion, Mexico remains the primary target,” […]
Cyber News