Cybercriminals Targeting Latin America with Sophisticated Phishing Scheme
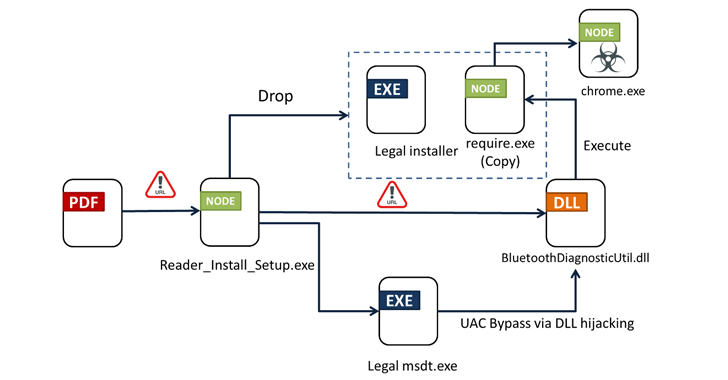
A new phishing campaign has set its eyes on the Latin American region to deliver malicious payloads to Windows systems. “The phishing email contained a ZIP file attachment that when extracted reveals an HTML file that leads to a malicious file download posing as an invoice,” Trustwave SpiderLabs researcher Karla Agregado said. The email message, […]
Cyber News