Critical Flaw in Rockwell Automation Devices Allows Unauthorized Access
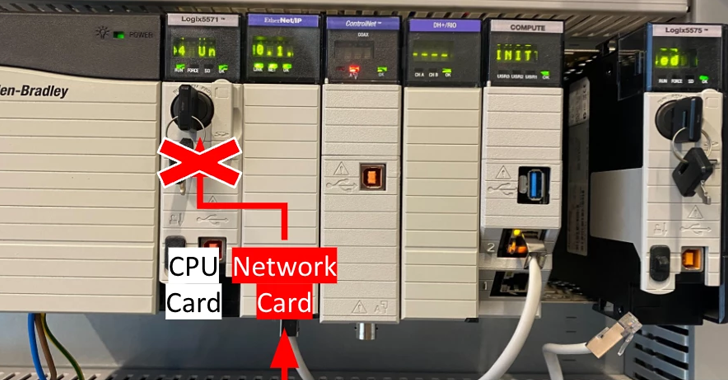
A high-severity security bypass vulnerability has been disclosed in Rockwell Automation ControlLogix 1756 devices that could be exploited to execute common industrial protocol (CIP) programming and configuration commands. The flaw, which is assigned the CVE identifier CVE-2024-6242, carries a CVSS v3.1 score of 8.4. “A vulnerability exists in the affected products that allows a threat […]
Cyber News