Ultralytics Supply-Chain Attack
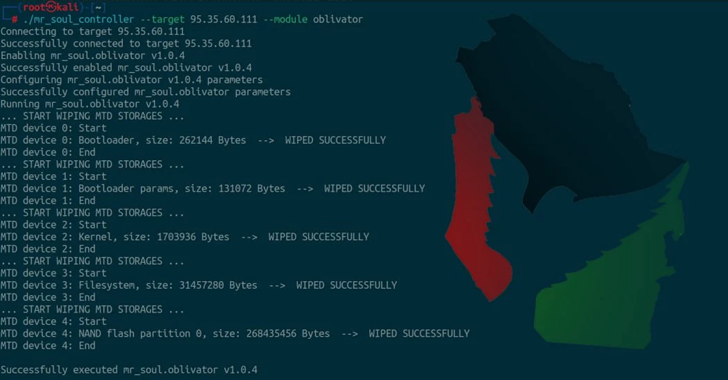
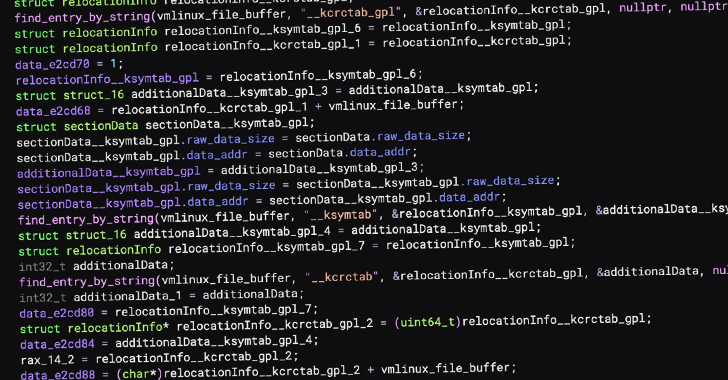
Last week, we saw a supply-chain attack against the Ultralytics AI library on GitHub. A quick summary: On December 4, a malicious version 8.3.41 of the popular AI library ultralytics —which has almost 60 million downloads—was published to the Python Package Index (PyPI) package repository. The package contained downloader code that was downloading the XMRig […]
Cyber News