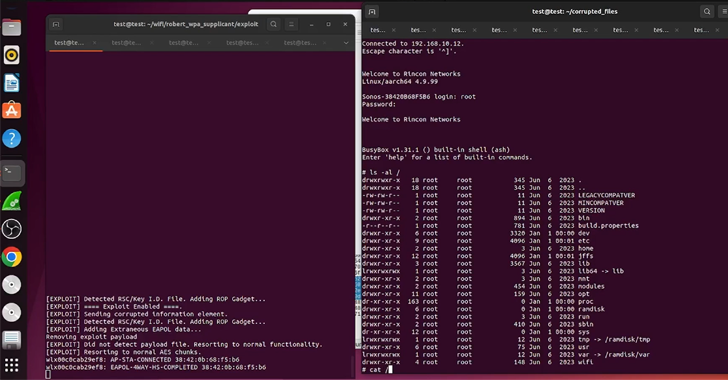
Sonos Speaker Flaws Could Have Let Remote Hackers Eavesdrop on Users
Cybersecurity researchers have uncovered weaknesses in Sonos smart speakers that could be exploited by malicious actors to clandestinely eavesdrop on users. The vulnerabilities “led to an entire break in the security of Sonos’s secure boot process across a wide range of devices and remotely being able to compromise several devices over the air,” NCC Group […]
Cyber News