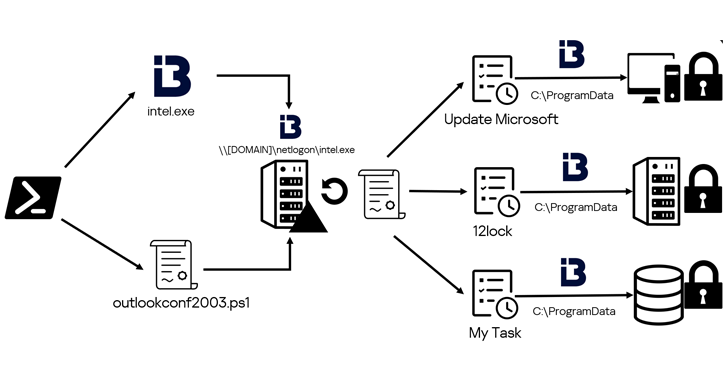
Chinese Hackers Exploit GeoServer Flaw to Target APAC Nations with EAGLEDOOR Malware
A suspected advanced persistent threat (APT) originating from China targeted a government organization in Taiwan, and possibly other countries in the Asia-Pacific (APAC) region, by exploiting a recently patched critical security flaw impacting OSGeo GeoServer GeoTools. The intrusion activity, which was detected by Trend Micro in July 2024, has been attributed to a threat actor […]
Cyber News