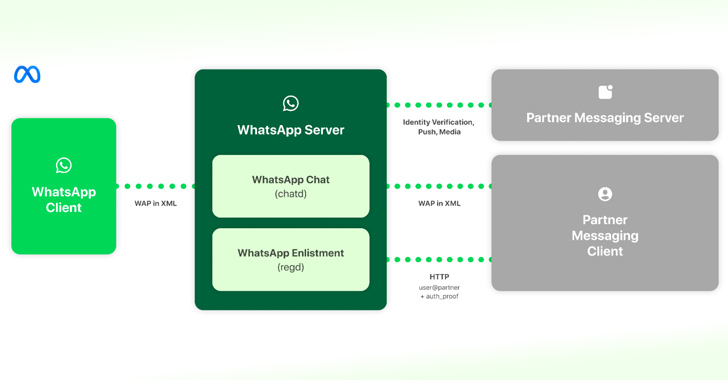
Meta Details WhatsApp and Messenger Interoperability to Comply with EU’s DMA Regulations
Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger with third-party messaging services as the Digital Markets Act (DMA) went into effect in the European Union. “This allows users of third-party providers who choose to enable interoperability (interop) to send and receive messages with opted-in users of either Messenger […]
Cyber News