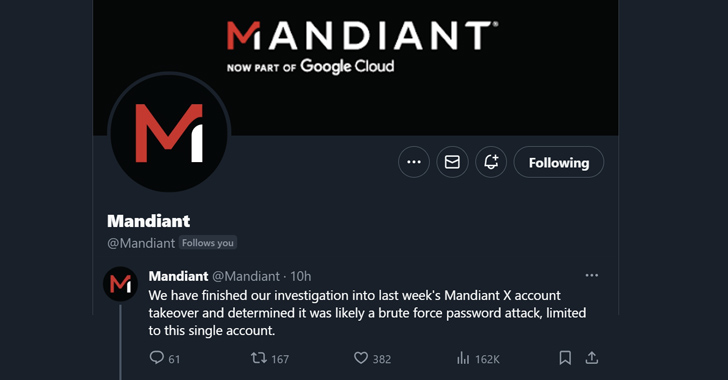
Security firm Mandiant says it didn’t have 2FA enabled on its hacked Twitter account
Anyone who works in computer security knows that they should have two-factor authentication (2FA) enabled on their accounts. 2FA provides an additional layer of security. A hacker might be able to guess, steal, or brute force the password on your accounts – but they won’t be able to gain access unless they also have a […]
Cyber News