New 5G Modem Flaws Affect iOS Devices and Android Models from Major Brands
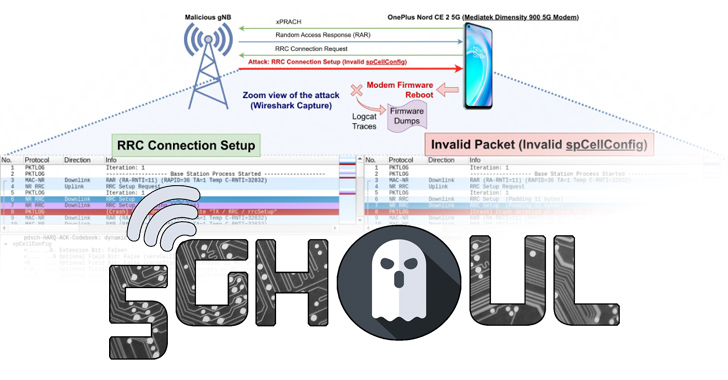
A collection of security flaws in the firmware implementation of 5G mobile network modems from major chipset vendors such as MediaTek and Qualcomm impact USB and IoT modems as well as hundreds of smartphone models running Android and iOS. Of the 14 flaws – collectively called 5Ghoul (a combination of “5G” and “Ghoul”) – 10 […]
Cyber News