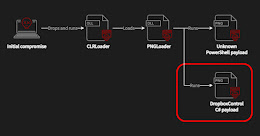
Worok Hackers Abuse Dropbox API to Exfiltrate Data via Backdoor Hidden in Images
A recently discovered cyber espionage group dubbed Worok has been found hiding malware in seemingly innocuous image files, corroborating a crucial link in the threat actor’s infection chain. Czech cybersecurity firm Avast said the purpose of the PNG files is to conceal a payload that’s used to facilitate information theft. “What is noteworthy is data collection from […]
Cyber News, Cyber Threat Trends