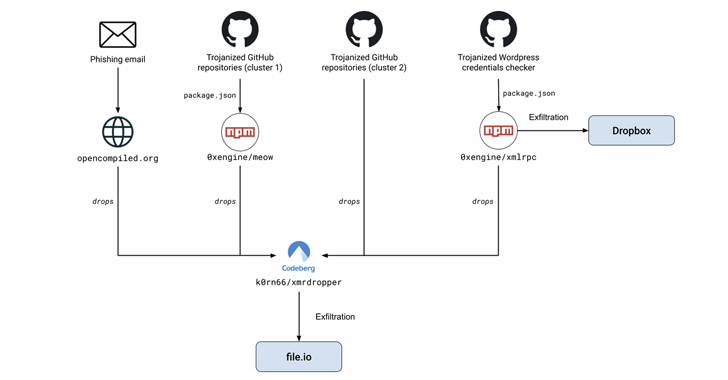
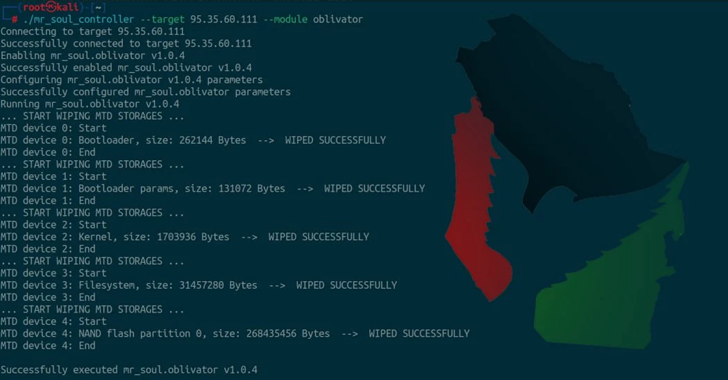
390,000+ WordPress Credentials Stolen via Malicious GitHub Repository Hosting PoC Exploits
A now-removed GitHub repository that advertised a WordPress tool to publish posts to the online content management system (CMS) is estimated to have enabled the exfiltration of over 390,000 credentials. The malicious activity is part of a broader attack campaign undertaken by a threat actor, dubbed MUT-1244 (where MUT refers to “mysterious unattributed threat”) by […]
Cyber News