Secure Email Threat Defense: Providing critical insight into business risk
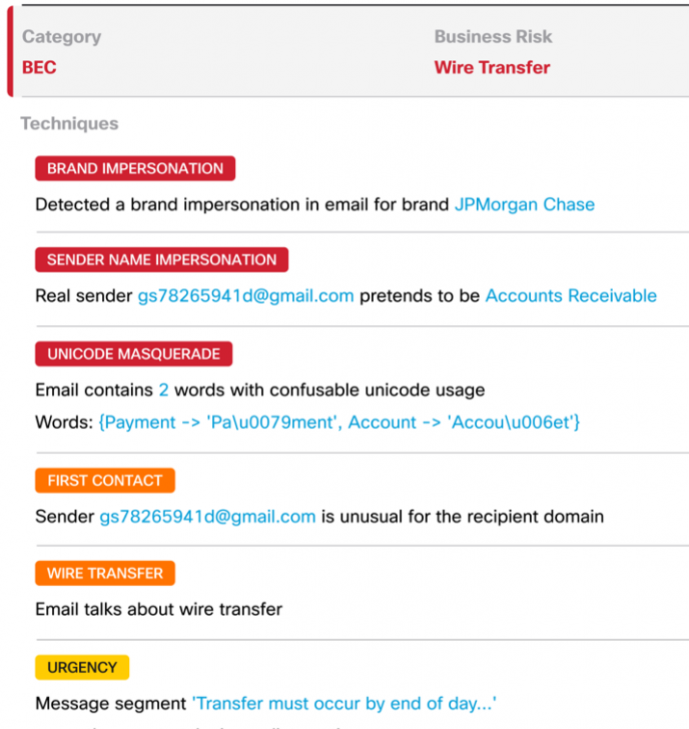
Attackers specifically craft business email compromise (BEC) and phishing emails using a combination of malicious techniques, expertly selected from an ever-evolving bag of tricks. They’ll use these techniques to impersonate a person or business that’s well-known to the targeted recipient and hide their true intentions, while attempting to avoid detection by security controls. As a […]
Cyber News, Cyber Threat Trends