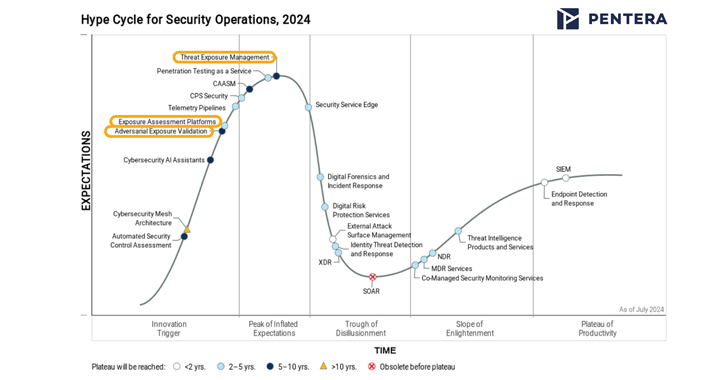
CTEM in the Spotlight: How Gartner’s New Categories Help to Manage Exposures
Want to know what’s the latest and greatest in SecOps for 2024? Gartner’s recently released Hype Cycle for Security Operations report takes important steps to organize and mature the domain of Continuous Threat Exposure Management, aka CTEM. Three categories within this domain are included in this year’s report: Threat Exposure Management, Exposure Assessment Platforms (EAP), […]
Cyber News