PLAYFULGHOST Delivered via Phishing and SEO Poisoning in Trojanized VPN Apps
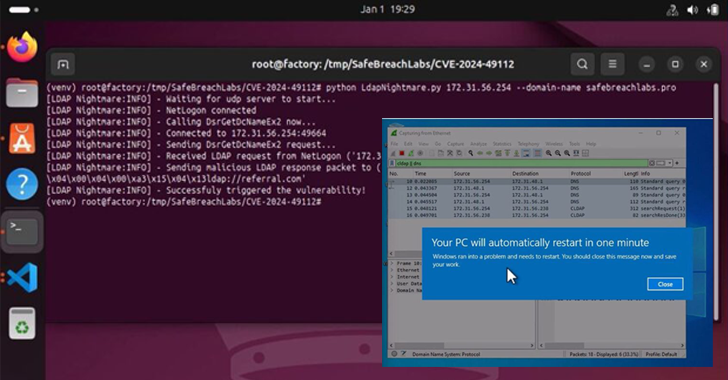
Cybersecurity researchers have flagged a new malware called PLAYFULGHOST that comes with a wide range of information-gathering features like keylogging, screen capture, audio capture, remote shell, and file transfer/execution. The backdoor, according to Google’s Managed Defense team, shares functional overlaps with a known remote administration tool referred to as Gh0st RAT, which had its source […]
Cyber News