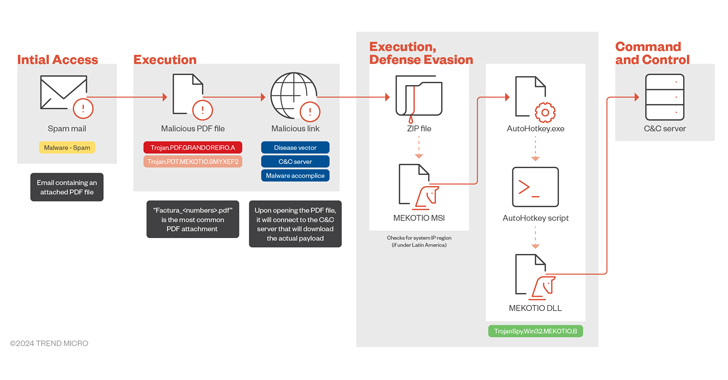
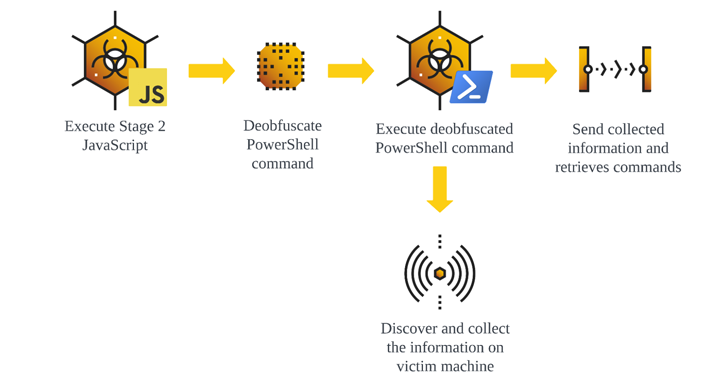
5 Key Questions CISOs Must Ask Themselves About Their Cybersecurity Strategy
Events like the recent massive CDK ransomware attack – which shuttered car dealerships across the U.S. in late June 2024 – barely raise public eyebrows anymore. Yet businesses, and the people that lead them, are justifiably jittery. Every CISO knows that cybersecurity is an increasingly hot topic for executives and board members alike. And when […]
Cyber News