Passwords are rarely appreciated until a security breach occurs; suffice to say, the importance of a strong password becomes clear only when faced with the consequences of a weak one. However, most end users are unaware of just how vulnerable their passwords are to the most common password-cracking methods. The following are the three common techniques for cracking passwords and how to

- February 26, 2025
- by Francis Schmuff
- Cyber News
- Less than a minute
- 109 Views
Related Post
- by Francis Schmuff
- June 6, 2025
New PathWiper Data Wiper Malware Disrupts Ukrainian Critical
A critical infrastructure entity within Ukraine was targeted by a previously unseen data wiper malware named PathWiper, according to new
- by Francis Schmuff
- June 5, 2025
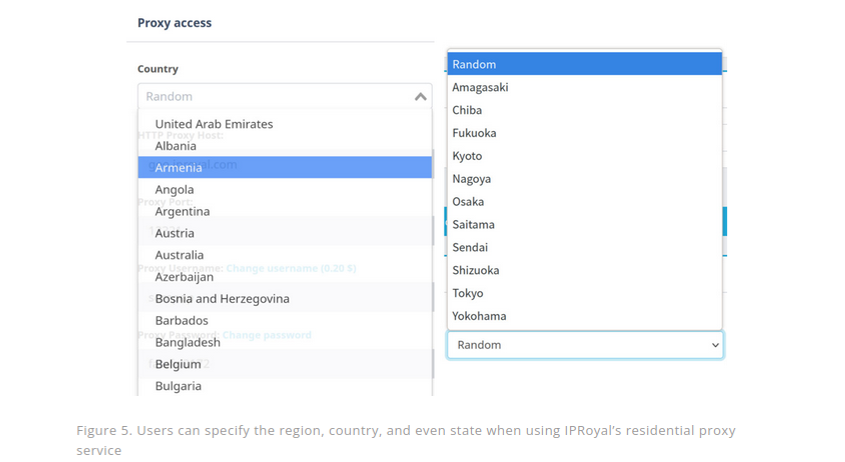
Proxy Services Feast on Ukraine’s IP Address Exodus
Image: Mark Rademaker, via Shutterstock. Ukraine has seen nearly one-fifth of its Internet space come under Russian control or sold
- by Francis Schmuff
- June 5, 2025
Popular Chrome Extensions Leak API Keys, User Data
Cybersecurity researchers have flagged several popular Google Chrome extensions that have been found to transmit data in HTTP and hard-code
- by Francis Schmuff
- June 5, 2025
Researchers Detail Bitter APT’s Evolving Tactics as Its
The threat actor known as Bitter has been assessed to be a state-backed hacking group that’s tasked with gathering intelligence