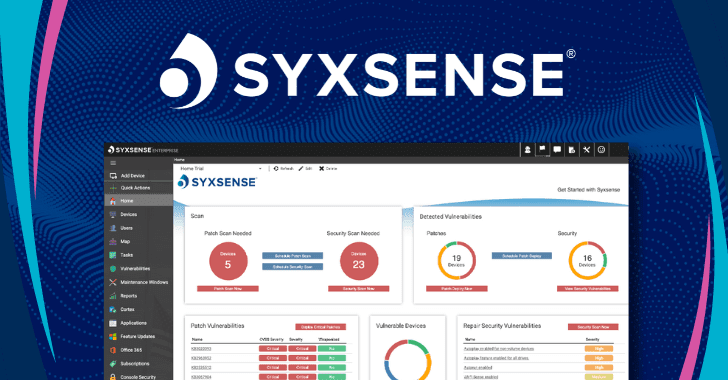
As threats grow and attack surfaces get more complex, companies continue to struggle with the multitude of tools they utilize to handle endpoint security and management. This can leave gaps in an enterprise’s ability to identify devices that are accessing the network and in ensuring that those devices are compliant with security policies. These gaps are often seen in outdated spreadsheets that
- March 8, 2023
- by
- Cyber News, Cyber Threat Trends
- Less than a minute
- 228 Views
Related Post
- by Francis Schmuff
- June 6, 2025
Friday Squid Blogging: Squid Run in Southern New
Southern New England is having the best squid run in years. As usual, you can also use this squid post
- by Francis Schmuff
- June 6, 2025
Hearing on the Federal Government and AI
On Thursday I testified before the House Committee on Oversight and Government Reform at a hearing titled “The Federal Government
- by Francis Schmuff
- June 6, 2025
New Atomic macOS Stealer Campaign Exploits ClickFix to
Cybersecurity researchers are alerting to a new malware campaign that employs the ClickFix social engineering tactic to trick users into
- by Francis Schmuff
- June 6, 2025
Report on the Malicious Uses of AI
OpenAI just published its annual report on malicious uses of AI. By using AI as a force multiplier for our



